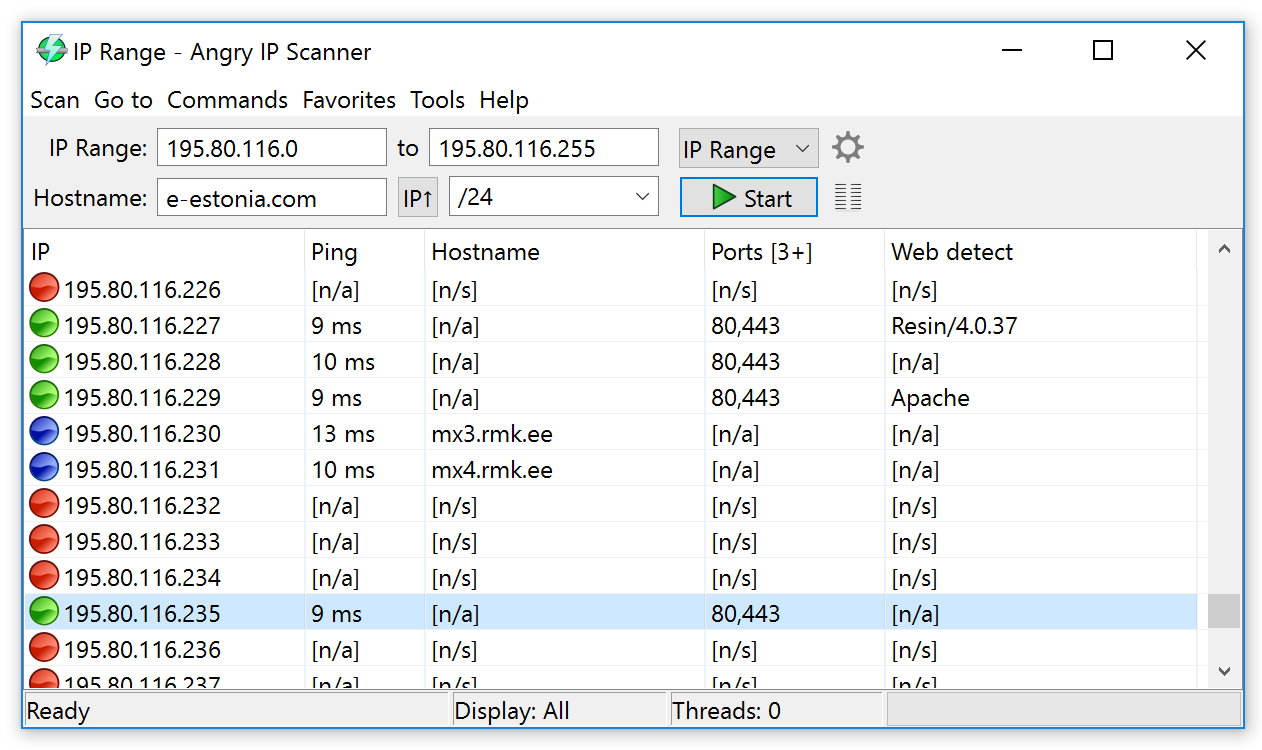
Download Zenmap - You can easily track the network activity, as well as the traffic on a specific website, based on the available hosts, with this application. Get Mac Address Of Local System Get Mac Address Of Remote But Same Network System. We can use Nmap to get mac address of a host if we are in the same network segment. $ sudo nmap -sP -n 192.168.122.0/24 Get Mac Address Of Remote But Same Network System Get Mac Address Of Remote System With Snmp. The more complicated way is using SNMP service. Basic Nmap Scan against IP or host. Now, if you want to scan a hostname, simply.
Unlike the software developed for Windows system, most of the applications installed in Mac OS X generally can be removed with relative ease. Zenmap 7.01 is a third party application that provides additional functionality to OS X system and enjoys a popularity among Mac users. However, instead of installing it by dragging its icon to the Application folder, uninstalling Zenmap 7.01 may need you to do more than a simple drag-and-drop to the Trash.
Download Mac App RemoverWhen installed, Zenmap 7.01 creates files in several locations. Generally, its additional files, such as preference files and application support files, still remains on the hard drive after you delete Zenmap 7.01 from the Application folder, in case that the next time you decide to reinstall it, the settings of this program still be kept. But if you are trying to uninstall Zenmap 7.01 in full and free up your disk space, removing all its components is highly necessary. Continue reading this article to learn about the proper methods for uninstalling Zenmap 7.01.
Manually uninstall Zenmap 7.01 step by step:
Most applications in Mac OS X are bundles that contain all, or at least most, of the files needed to run the application, that is to say, they are self-contained. Thus, different from the program uninstall method of using the control panel in Windows, Mac users can easily drag any unwanted application to the Trash and then the removal process is started. Despite that, you should also be aware that removing an unbundled application by moving it into the Trash leave behind some of its components on your Mac. To fully get rid of Zenmap 7.01 from your Mac, you can manually follow these steps:
1. Terminate Zenmap 7.01 process(es) via Activity Monitor
Before uninstalling Zenmap 7.01, you’d better quit this application and end all its processes. If Zenmap 7.01 is frozen, you can press Cmd +Opt + Esc, select Zenmap 7.01 in the pop-up windows and click Force Quit to quit this program (this shortcut for force quit works for the application that appears but not for its hidden processes).
Open Activity Monitor in the Utilities folder in Launchpad, and select All Processes on the drop-down menu at the top of the window. Select the process(es) associated with Zenmap 7.01 in the list, click Quit Process icon in the left corner of the window, and click Quit in the pop-up dialog box (if that doesn’t work, then try Force Quit).
2. Delete Zenmap 7.01 application using the Trash

First of all, make sure to log into your Mac with an administrator account, or you will be asked for a password when you try to delete something.
Open the Applications folder in the Finder (if it doesn’t appear in the sidebar, go to the Menu Bar, open the “Go” menu, and select Applications in the list), search for Zenmap 7.01 application by typing its name in the search field, and then drag it to the Trash (in the dock) to begin the uninstall process. Alternatively you can also click on the Zenmap 7.01 icon/folder and move it to the Trash by pressing Cmd + Del or choosing the File and Move to Trash commands.
For the applications that are installed from the App Store, you can simply go to the Launchpad, search for the application, click and hold its icon with your mouse button (or hold down the Option key), then the icon will wiggle and show the “X” in its left upper corner. Click the “X” and click Delete in the confirmation dialog.
Download Mac App Remover3. Remove all components related to Zenmap 7.01 in Finder
Though Zenmap 7.01 has been deleted to the Trash, its lingering files, logs, caches and other miscellaneous contents may stay on the hard disk. For complete removal of Zenmap 7.01, you can manually detect and clean out all components associated with this application. You can search for the relevant names using Spotlight. Those preference files of Zenmap 7.01 can be found in the Preferences folder within your user’s library folder (~/Library/Preferences) or the system-wide Library located at the root of the system volume (/Library/Preferences/), while the support files are located in '~/Library/Application Support/' or '/Library/Application Support/'.
Open the Finder, go to the Menu Bar, open the “Go” menu, select the entry:|Go to Folder... and then enter the path of the Application Support folder:~/Library
Search for any files or folders with the program’s name or developer’s name in the ~/Library/Preferences/, ~/Library/Application Support/ and ~/Library/Caches/ folders. Right click on those items and click Move to Trash to delete them.
Meanwhile, search for the following locations to delete associated items:
- /Library/Preferences/
- /Library/Application Support/
- /Library/Caches/
Besides, there may be some kernel extensions or hidden files that are not obvious to find. In that case, you can do a Google search about the components for Zenmap 7.01. Usually kernel extensions are located in in /System/Library/Extensions and end with the extension .kext, while hidden files are mostly located in your home folder. You can use Terminal (inside Applications/Utilities) to list the contents of the directory in question and delete the offending item.
4. Empty the Trash to fully remove Zenmap 7.01
What Is Zenmap Used For
If you are determined to delete Zenmap 7.01 permanently, the last thing you need to do is emptying the Trash. To completely empty your trash can, you can right click on the Trash in the dock and choose Empty Trash, or simply choose Empty Trash under the Finder menu (Notice: you can not undo this act, so make sure that you haven’t mistakenly deleted anything before doing this act. If you change your mind, before emptying the Trash, you can right click on the items in the Trash and choose Put Back in the list). In case you cannot empty the Trash, reboot your Mac.
Download Mac App RemoverTips for the app with default uninstall utility:
You may not notice that, there are a few of Mac applications that come with dedicated uninstallation programs. Though the method mentioned above can solve the most app uninstall problems, you can still go for its installation disk or the application folder or package to check if the app has its own uninstaller first. If so, just run such an app and follow the prompts to uninstall properly. After that, search for related files to make sure if the app and its additional files are fully deleted from your Mac.
Automatically uninstall Zenmap 7.01 with MacRemover (recommended):
No doubt that uninstalling programs in Mac system has been much simpler than in Windows system. But it still may seem a little tedious and time-consuming for those OS X beginners to manually remove Zenmap 7.01 and totally clean out all its remnants. Why not try an easier and faster way to thoroughly remove it?
If you intend to save your time and energy in uninstalling Zenmap 7.01, or you encounter some specific problems in deleting it to the Trash, or even you are not sure which files or folders belong to Zenmap 7.01, you can turn to a professional third-party uninstaller to resolve troubles. Here MacRemover is recommended for you to accomplish Zenmap 7.01 uninstall within three simple steps. MacRemover is a lite but powerful uninstaller utility that helps you thoroughly remove unwanted, corrupted or incompatible apps from your Mac. Now let’s see how it works to complete Zenmap 7.01 removal task.
1. Download MacRemover and install it by dragging its icon to the application folder.
2. Launch MacRemover in the dock or Launchpad, select Zenmap 7.01 appearing on the interface, and click Run Analysis button to proceed.
3. Review Zenmap 7.01 files or folders, click Complete Uninstall button and then click Yes in the pup-up dialog box to confirm Zenmap 7.01 removal.
The whole uninstall process may takes even less than one minute to finish, and then all items associated with Zenmap 7.01 has been successfully removed from your Mac!
Benefits of using MacRemover:
MacRemover has a friendly and simply interface and even the first-time users can easily operate any unwanted program uninstallation. With its unique Smart Analytic System, MacRemover is capable of quickly locating every associated components of Zenmap 7.01 and safely deleting them within a few clicks. Thoroughly uninstalling Zenmap 7.01 from your mac with MacRemover becomes incredibly straightforward and speedy, right? You don’t need to check the Library or manually remove its additional files. Actually, all you need to do is a select-and-delete move. As MacRemover comes in handy to all those who want to get rid of any unwanted programs without any hassle, you’re welcome to download it and enjoy the excellent user experience right now!
This article provides you two methods (both manually and automatically) to properly and quickly uninstall Zenmap 7.01, and either of them works for most of the apps on your Mac. If you confront any difficulty in uninstalling any unwanted application/software, don’t hesitate to apply this automatic tool and resolve your troubles.
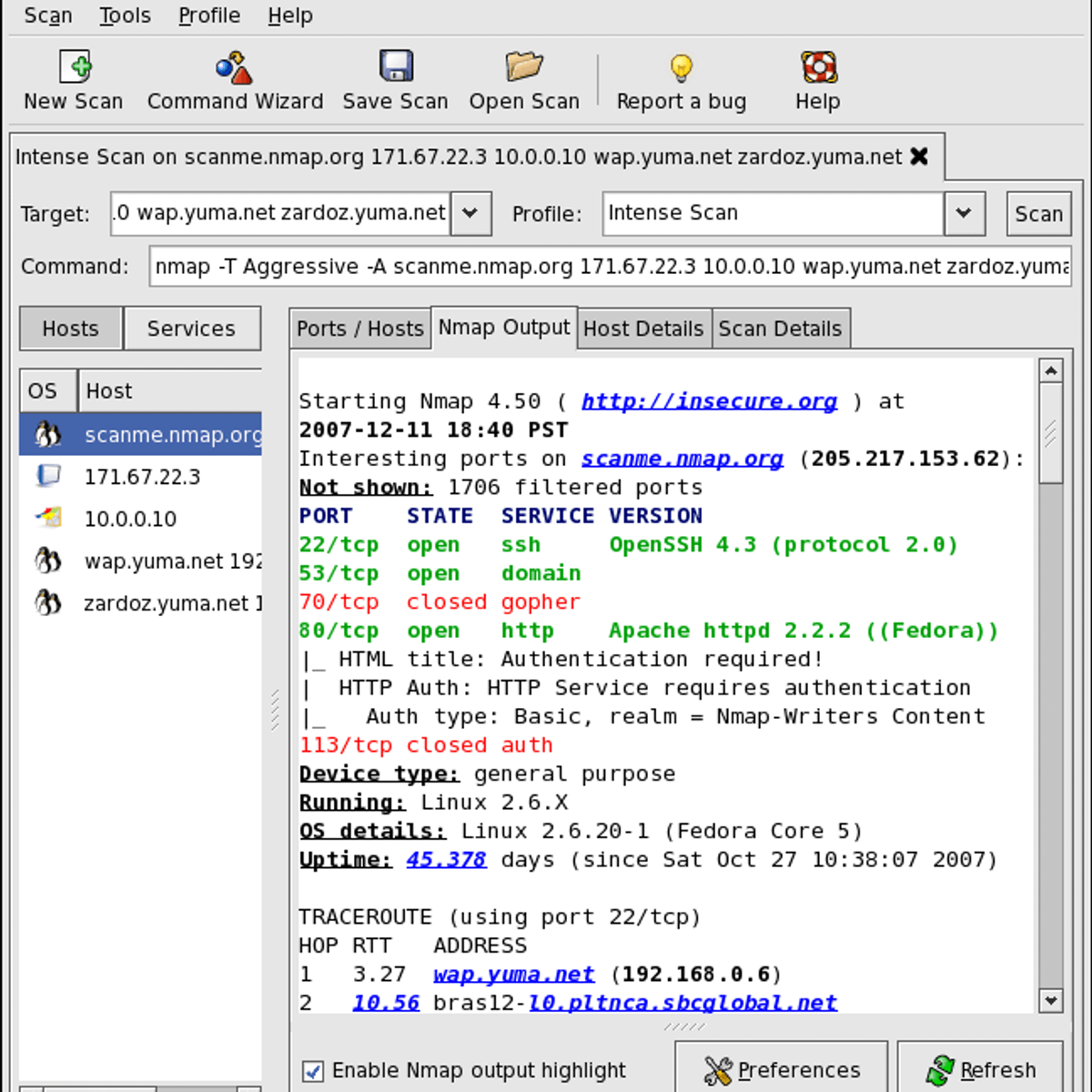
Download Mac App RemoverSome of this tool’s best features are that it’s open-source, free, multi-platform and receives constant updates each year. It also has a big plus: it’s one of the most complete host and network scanners available. It includes a large set of options to enhance your scanning and mapping tasks, and brings with it an incredible community and comprehensive documentation to help you understand this tool from the very start. Nmap can be used to:
- Create a complete computer network map.
- Find remote IP addresses of any hosts.
- Get the OS system and software details.
- Detect open ports on local and remote systems.
- Audit server security standards.
- Find vulnerabilities on remote and local hosts.
It was mentioned in the Top 20 OSINT Tools article we published, and today we’ll explore a little bit more about this essential security tool with some practical terminal-based Nmap commands.
Best 15 Nmap command examples
Let’s get to know a few useful command-line based scans that can be performed using Nmap.
1. Basic Nmap Scan against IP or host
nmap 1.1.1.1
Now, if you want to scan a hostname, simply replace the IP for the host, as you see below:

nmap cloudflare.com
These kinds of basic scans are perfect for your first steps when starting with Nmap.
2. Scan specific ports or scan entire port ranges on a local or remote server
nmap -p 1-65535 localhost
In this example, we scanned all 65535 ports for our localhost computer.
Nmap is able to scan all possible ports, but you can also scan specific ports, which will report faster results. See below:
nmap -p 80,443 8.8.8.8
3. Scan multiple IP addresses
Let’s try to scan multiple IP addresses. For this you need to use this syntax:
nmap 1.1.1.1 8.8.8.8
You can also scan consecutive IP addresses:
nmap -p 1.1.1.1,2,3,4
This will scan 1.1.1.1, 1.1.1.2, 1.1.1.3 and 1.1.1.4.
4. Scan IP ranges
You can also use Nmap to scan entire CIDR IP ranges, for example:
nmap -p 8.8.8.0/28
This will scan 14 consecutive IP ranges, from 8.8.8.1 to 8.8.8.14.
An alternative is to simply use this kind of range:
nmap 8.8.8.1-14
You can even use wildcards to scan the entire C class IP range, for example:
nmap 8.8.8.*
This will scan 256 IP addresses from 8.8.8.1 to 8.8.8.256.
If you ever need to exclude certain IPs from the IP range scan, you can use the “–exclude” option, as you see below:
nmap -p 8.8.8.* --exclude 8.8.8.1
5. Scan the most popular ports
Using “–top-ports” parameter along with a specific number lets you scan the top X most common ports for that host, as we can see:
nmap --top-ports 20 192.168.1.106
Replace “20” with the desired number. Output example:
6. Scan hosts and IP addresses reading from a text file
In this case, Nmap is also useful to read files that contain hosts and IPs inside.
Let’s suppose you create a list.txt file that contains these lines inside:
The “-iL” parameter lets you read from that file, and scan all those hosts for you:
nmap -iL list.txt
7. Save your Nmap scan results to a file
On the other hand, in the following example we will not be reading from a file, but exporting/saving our results into a text file:
nmap -oN output.txt securitytrails.com
Nmap has the ability to export files into XML format as well, see the next example:
nmap -oX output.xml securitytrails.com
Zenmap Download For Mac
8. Disabling DNS name resolution
If you need to speed up your scans a little bit, you can always choose to disable reverse DNS resolution for all your scans. Just add the “-n” parameter.
See the difference with a normal DNS-resolution enabled scan:
9. Scan + OS and service detection with fast execution
Using the “-A” parameter enables you to perform OS and service detection, and at the same time we are combining this with “-T4” for faster execution. See the example below:
nmap -A -T4 cloudflare.com
This is the output we got for this test:
10. Detect service/daemon versions
This can be done by using -sV parameters
nmap -sV localhost
As you can see here:
11. Scan using TCP or UDP protocols
One of the things we love most about Nmap is the fact that it works for both TCP and UDP protocols. And while most services run on TCP, you can also get a great advantage by scanning UDP-based services. Let’s see some examples.
Standard TCP scanning output:
UDP scanning results using “-sU” parameter:
12. CVE detection using Nmap
One of Nmap’s greatest features that not all the network and systems administrators know about is something called “Nmap Scripting Engine” (known as NSE). This scripting engine allows users to use a pre-defined set of scripts, or write their own using Lua programming language.
Using NSE is crucial in order to automate system and vulnerability scans. For example, if you want to run a full vulnerability test against your target, you can use these parameters:
nmap -Pn --script vuln 192.168.1.105
Output example:
As you can see, in this vulnerability test we were able to detect one CVE (Slowloris DOS attack).
Stay in the loop with the best infosec news, tips and tools
Follow us on Twitter to receive updates!
13. Launching DOS with Nmap
Nmap features never seem to end, and thanks to the NSE, that even allows us to launch DOS attacks against our network testings.
In our previous example (#12) we found the host was vulnerable to Slowloris attack, and now we’ll try to exploit that vulnerability by launching a DOS attack in a forever loop:
14. Launching brute force attacks
NSE is really fascinating – it contains scripts for everything you can imagine. See the next three examples of BFA against WordPress, MSSQL, and FTP server:
WordPress brute force attack:
Brute force attack against MS-SQL:
FTP brute force attack:
nmap --script ftp-brute -p 21 192.168.1.105
15. Detecting malware infections on remote hosts
Nmap is able to detect malware and backdoors by running extensive tests on a few popular OS services like on Identd, Proftpd, Vsftpd, IRC, SMB, and SMTP. It also has a module to check for popular malware signs inside remote servers and integrates Google’s Safe Browsing and VirusTotal databases as well.
A common malware scan can be performed by using:
nmap -sV --script=http-malware-host 192.168.1.105
Or using Google’s Malware check:
nmap -p80 --script http-google-malware infectedsite.com
Output example:
Nmap is one of the most complete and accurate port scanners used by infosec professionals today. With it, you can perform simple port scan tasks or use its powerful scripting engine to launch DOS attacks, detect malware or brute force testings on remote and local servers.
Today we covered the top fifteen Nmap commands to scan remote hosts, but there’s a lot more to discover if you’re starting to use Nmap in your OSINT strategy.
If you also need to map domains, IPs and discover DNS zones, try our SecurityTrails toolkit, or grab a free API account today.
Find all your DNS records, IP addresses, Ports and Domain names in seconds — without running any scans!Fill out the form to learn how SurfaceBrowser™ can help you identify your attack surface.Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. Since joining SecurityTrails in 2017 he’s been our go-to for technical server security and source intelligence info.
Get the best cybersec research, news, tools,
and interviews with industry leaders
